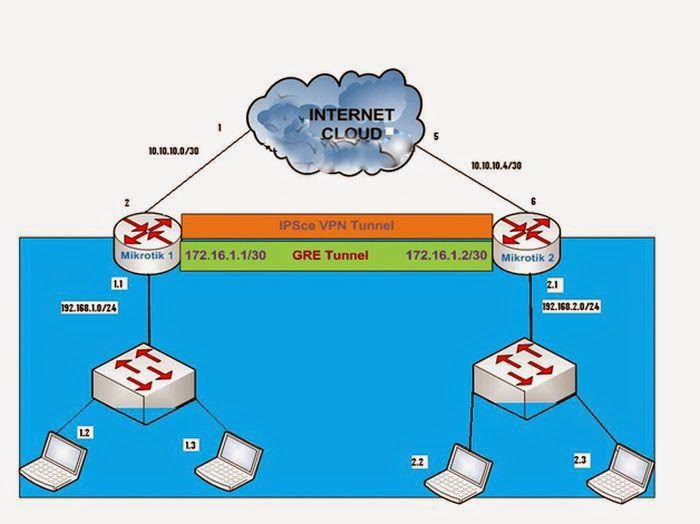
Mikrotik-1GRE Tunnel and IP Address Configuration:
MikroTik1> ip address add address=10.10.10.2/30 interface=ether1
MikroTik1> ip address add address=192.168.1.1/24 interface=ether5
MikroTik1> interface gre add name= gre-tunnel1 local-address=10.10.10.2 remote-address=10.10.10.6
MikroTik1> ip address add address=172.16.1.1/30 interface= gre-tunnel1
Mikrotik-1 Router IPSec VPN Configuration:
MikroTik-1>ip ipsec peer>add address=10.10.10.6/32:500 auth-method=pre-shared-key secret=”password”
generate-policy=no exchange-mode=main send-initial-contact=yes
nat-traversal=no proposal-check=obey hash-algorithm=sha1
enc-algorithm=3des dh-group=modp1024 lifetime=1d lifebytes=0
dpd-interval=disable-dpd dpd-maximum-failures=1
MikroTik-1> ip ipsec policy>add src-address=10.10.10.2/32:any dst-address=10.10.10.6/32:any
protocol=all action=encrypt level=require ipsec-protocols=esp tunnel=yes
sa-src-address=10.10.10.2 sa-dst-address=10.10.10.6 proposal=default
priority=0
MikroTik-1 >ip ipsec proposal>add name=”default” auth-algorithms=sha1 enc-algorithms=3des lifetime=30m pfs-group=modp1024
Mikroitk-1 Router OSPF Configuration:
MikroTik-1> routing ospf> network add network=192.168.1.0/24 area=backbone
MikroTik-1> routing ospf> network add network=172.16.1.0/30 area=backbone
Mikrotik-2 GRE Tunnel and IP Address Configuration:
MikroTik2# ip address add address=10.10.10.6/30 interface=ether1
MikroTik2# ip address add address=192.168.2.1/24 interface=ether5
MikroTik2# interface gre add name= gre-tunnel1 local-address=10.10.10.6 remote-address=10.10.10.2
MikroTik2# ip address add address=172.16.1.2/30 interface= gre-tunnel1
Mikrotik-2 Router IPSec VPN Configuration:
MikroTik-2#ip ipsec peer>add address=10.10.10.2/32:500 auth-method=pre-shared-key secret=”password”
generate-policy=no exchange-mode=main send-initial-contact=yes
nat-traversal=no proposal-check=obey hash-algorithm=sha1
enc-algorithm=3des dh-group=modp1024 lifetime=1d lifebytes=0
dpd-interval=disable-dpd dpd-maximum-failures=1
MikroTik-2#ip ipsec policy>add src-address=10.10.10.6/32:any dst-address=10.10.10.2/32:any
protocol=all action=encrypt level=require ipsec-protocols=esp tunnel=yes
sa-src-address=10.10.10.6 sa-dst-address=10.10.10.2 proposal=default
priority=0
MikroTik-2#ip ipsec proposal>add name=”default” auth-algorithms=sha1 enc-algorithms=3des lifetime=30m pfs-group=modp1024
Mikroitk-2 Router OSPF Configuration:
MikroTik-2#routing ospf> network add network=192.168.2.0/24 area=backbone
MikroTik-2#routing ospf> network add network=172.16.1.0/30 area=backbone



Leave a Reply
You must be logged in to post a comment.