VLAN Concept:
The virtual local area network (VLAN) is a group of devices one or more Local Area Network. A Local Area Network (LAN) was primitively defined as a network of computers placed within the equal area. Now, Local Area Networks are specified as a separate broadcast domain.
This implies that whenever a user broadcasts information on LAN, the broadcast will be accepted by every extra user on the LAN. Broadcasts are precluded from allowing a Local area network by applying a router. The disfavor of this formula is routers generally take a lot of time to procedure entrance data compared to a bridge or a switch.
More significantly, the constitution of broadcast domains depends upon the active connection of the devices on the network. Virtual Local Area Networks (VLAN’s) were built up alternatively solution to applying routers to control broadcast traffic.
What is VLAN ?:
In a conventional LAN, workstations are associated with each additional by implies of a hub or a repeater. These devices distribute any Entrance data throughout the network. All the same, whenever 2 people effort to send information simultaneously, a collision will Pass and altogether the broadcast data will be destroyed.
Sometimes the collision has occurred, it will bear on to be diffused throughout the network of hubs and repeaters. The master selective information will consequently need to be resent after waiting for the collision to be decided thereby obtaining an important wastage of time and resources. To forbid collisions from itinerant through all the workstations inward the network, a bridge or a switch can be applied.
These devices won’t advancing collisions but will permit broadcasts (to all users in the network) and multicasts to a pre-specified group of users to pass through. A router may be used to forbid propagates and multicasts from traveling through with the network.
How to VLAN work?:
When a LAN span receives data from a workstation, it tags the data with a VLAN identifier pointing to the VLAN from which the data arrived. This is called denotative marking. It’s as well potential to decide to which VLAN the data accepted consists of applying Absolute tagging.
In inexplicit marking the data is not marked, but the VLAN from which the data followed is found free-based on additional information similar to the port on which the data came. Marking can be found on the port from which it arrived, the author Media Access Control (MAC) area, the source network address, or another area or compounding of fields.
VLAN’s are separated founded on the process wont to be able to do the marking of data, applying any of the techniques, the bridge would have to continue an updated database controlling mapping between VLAN’s and whichever area is applied for marking. For example, if tracking is by the port, the database should suggest which ports consist to which VLAN. This database is named a trickling database.
Bridges would have to be able to sustain this database and also to make a point that altogether the bridges about the LAN have equal data in each of their databases. The bridge limits wherever the data is to go adjacent founded on convention LAN procedures. At one time the bridge Decides where the data is to go,
it immediately asks to find out whether the VLAN identifier should be expanded the data and broadcast. If the data is to attend a device that acknowledges about VLAN carrying out (VLAN-aware), the VLAN identifier is increased the data. If it’s going to a device that has no cognition of VLAN carrying out (VLAN-unaware), the bridge bases the data without the VLAN identifier
Why use VLAN’s:
1) Performance:
inward networks where traffic belongs to a high-pressure portion of broadcasts and multicasts, VLAN’s can concentrate the require to send such traffic to unessential goals.
For example, in a broadcast domain belonging to ten users, whenever the broadcast traffic is destined alone for 5 of the users, then identifying those 5 users on an apart VLAN can abbreviate traffic equated to switches, routers expect several actioning of entering traffic.
As the volume of traffic transiting the routers’ additions, so does the response time in the routers, which consequences in abbreviated performance.
2) Formation of Virtual Workgroups:
Nowadays, it is basic to determine cross-functional production evolution teams with members from other departments such as marketing, sales, accounting, and IT.
These workgroups are normally defined for a curt period of time. During this period, communicating between members of the Workgroup will be high. To check broadcasts and multicasts inside the Workgroup, a VLAN can be set up for it. With VLAN’s it’s simpler to direct members of a Workgroup jointly. Without VLAN’s,
the alone process this would be potential is to physically move totally the members of the workgroup closer together. However, virtual workgroups don’t come without problems.
Consider the position wherever one user of the Workgroup is on the 4th floor of a constricting, and the additional Workgroup members are on the 2d level. Imaginations specified a printer would be placed on the second floor, which would be awkward for the alone 4th-floor user.
3. Easy Administration:
Seventy percentage of network costs are a ensue of adds, moves, and alterations of users in the network. All-time a user is pulled in a local area network, recabling, newly base covering, and reconfiguration of hubs and routers convert essential. A few of these chores can be easy with the apply of VLANs.
If a user is acting inside a VLAN, reconfiguration of routers is unneeded. Additionally, depending on the case of VLAN, extra administrative work can be contracted or reject.
4) Reduced Cost:
VLAN’s force out be used to produce broadcast areas that excrete the motivation for costly routers. price deliveries consequence from lower requirements for valuable network advances and a lot on this network.
5) Security:
Periodically, sensible data mayhap broadcast on a network. Inch such cases, identifying alone those users who force out have access to that data on a VLAN can concentrate the happens of an outsider earning approach to the data.
VLAN’s can as well be used to contain broadcast areas, bring about firewalls, limit approach, and inform the network handler of an intrusion. Certificate of sensible data is separated from the balance of the network, diminishing the opportunities of confidential information violates.
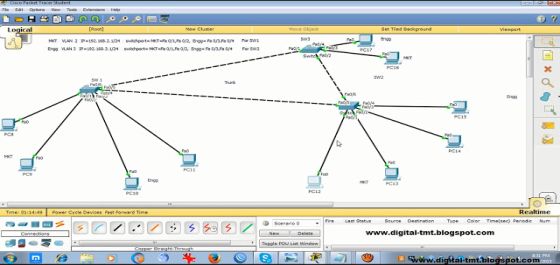
VLAN configuration step by step with video tutorial:
Switch1:
======
Switch1>enable
Switch1#configure t
Switch1(config)#vlan 2
Switch1(config-vlan)#name Engg
Switch1(config-vlan)#vlan 3
Switch1(config-vlan)#name mkt
Switch1(config)#int fa 0/1
Switch1(config-if)#switchport access vlan 2
Switch1(config-if)#int fa 0/2
Switch1(config-if)#switchport access vlan 2
Switch1(config)#int fa 0/3
Switch1(config-if)#switchport access vlan 3
Switch1(config)#int fa 0/4
Switch1(config-if)#switchport access vlan 3
For trunk port configuration:
Switch1(config)#int fa 0/5
Switch1(config-if)#switchport mode trunk
Switch1#show int trunk
Switch1(config)#int range fa 0/1 -4
Switch1(config-if-range)#switchport mode access
switch2:
======
Switch2#show vlan brief
Switch2>enable
Switch2#configure terminal
Switch2(config)#vlan 2
Switch2(config-vlan)#name MKT
Switch2(config-vlan)#vlan 3
Switch2(config-vlan)#name Engg
Switch2(config)#int range fa 0/1 -2
Switch2(config-if-range)#switchport access vlan 2
Switch2(config-if-range)#switchport mode access
Switch2(config)#int range fa 0/3 -4
Switch2(config-if-range)#switchport acces vlan 3
Switch2(config-if-range)#switchport mode acces
Switch 3:
======
Switch3>enable
Switch3#configure terminal
Switch3(config)#vlan 2
Switch3(config-vlan)#name MKT
Switch3(config-vlan)#vlan 3
Switch3(config-vlan)#name Engg
Switch3(config)#int fa 0/3
Switch3(config-if)#switchport access vlan 2
Switch3(config)#int fa 0/4
Switch3(config-if)#switchport access vlan 3
For trunk port configuration:
Switch3(config)#int fa 0/1
Switch3(config-if)#switchport mode trunk
Switch3(config)#int fa 0/2
Switch3(config-if)#switchport mode trunk
Switch3(config)#int range fa 0/3 -4
Switch3(config-if-range)#switchport mode access



Leave a Reply
You must be logged in to post a comment.